Cyber Security
Important Security Warning: Beware of Phishing Emails
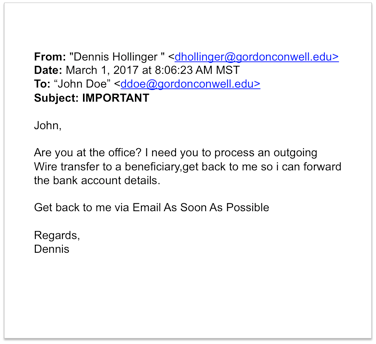
We have noticed a recent increase in the number of “phishing” emails coming to Gordon-Conwell email addresses. Phishing emails are scam emails designed to appear authentic; they attempt to deceive recipients into providing sensitive personal information by masquerading as people or organizations they know and trust. This detailed article from the Privacy Rights Clearinghouse has valuable tips for how to identify phishing emails and protect yourself and your personal account information from these attempts at identity theft: https://www.privacyrights.org/blog/watch-out-phishing-emails-attempting-capture-your-personal-information
Below is a 2-PART series titled
- PART 1: How do I figure out whether an external email is suspicious?
- PART 2: How do I figure out whether a Gordon-Conwell email is suspicious?
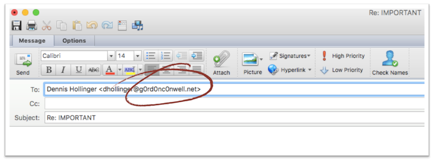
We hope that this will help you discern if you have received an email from a cyber-intruder. If you receive an email that appears to come from a trusted source but sounds suspicious and/or asks for personal information, please take precautions. Do not reply to the email, click any links in the email, or open any attached files. Instead, go straight to the purported source to verify the request (by phone or in person), and please forward the suspicious email to [email protected] for review.